PE (Portable Executable) File Format: Introduction
·3 mins
Table of Contents

Introduction #
-
Malware analysis is a valuable skill set that can benefit a variety of professionals within the Cybersecurity domain, from blue teamers to red teamers which is why over the past few weeks, I’ve dedicated my efforts to an in-depth exploration of the topic.
-
Today’s spotlight is on
Portable Executable (PE)format, our backstage pass into the inner workings of Windows binaries. -
We are going to start with general concepts then gradually dive into the details in future blog posts.
PE Files #
- PE is a
file formatforexecutables, object code, DLLs, etc.used in 32-bit and 64-bit versions of Windows operating systems, and inUEFIenvironments. - The format is a data structure that encapsulates the information necessary for the Windows OS loader to manage the wrapped
executable code.
Structure Overview #
- The standard structure of a PE file adheres to the diagram provided below.
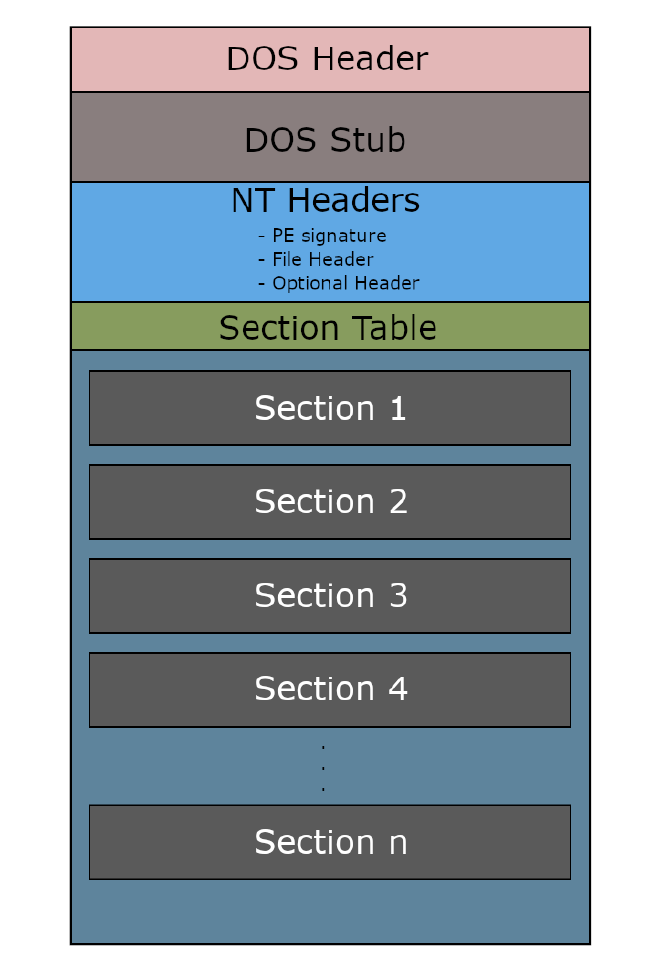
- Upon loading a binary into the
pebeartool and inspecting its structure, we observe that the binary precisely follows the outlined structure in the aforementioned diagram.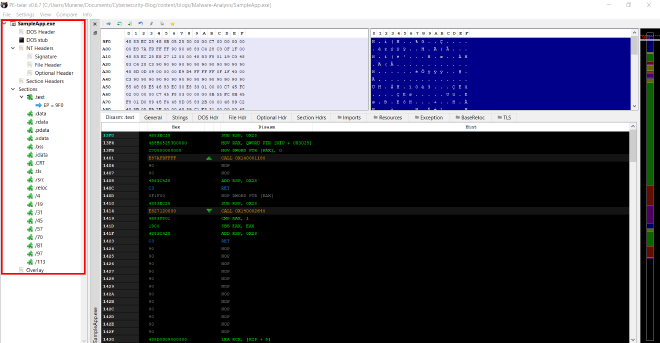
DOS Header #
- It is a 64 bytes of size structure found at the beginning of executable files and it contains information that the OS uses to load and execute the program.
DOS Stub #
- Following the DOS header is the DOS stub, a compact MS-DOS 2.0-compatible executable. When executed in DOS mode, this stub simply outputs an error message stating,
This program cannot be run in DOS mode.
NT Headers #
PE Signature #
- The PE Signature is a 32-bit signature represented by the ASCII characters
PEand the null character (0x00). - When these characters are found at the specified location in the file, it indicates to the operating system that the file follows the PE file format.
COFF File Header #
- COFF stands for
Common Object File Format. - The “COFF” Header, stores object code of the executable. Object code is what helps to compile the program into an executable.
Optional Header #
- Every image file has an optional header that provides information to the loader.
- This header is optional in the sense that some files (specifically, object files) do not have it.
- For image files, this header is required. An object file can have an optional header, but generally this header has no function in an object file except to increase its size.
Section Table #
- This table immediately follows the optional header, if any. This positioning is required because the file header does not contain a direct pointer to the section table.
- It is an array of Image Section Headers, there is a section header for every section in the PE file.
- Each header contains information about the section it refers to.
Sections #
- Sections store the essential contents of the file, encompassing
data,resources, and the program’sactual code. Multiple sections exist, each serving a distinct purpose within the file.
Conclusion #
- In this post, we provided a fundamental overview of the PE file structure and briefly discussed its main components. Subsequent posts will delve into each of these elements with a more in-depth exploration.