SheHacks KE CTF 2023
·2 mins

Table of Contents
Introduction #
- Took part in the SheHacks CTF 2023 hosted by eKRAAL Innovation Hub on 22nd September 2023 - 23rd September 2023, where our team emerged position 6/82. The CTF was a jeopardy style one, and this is the writeup for the challenges that I solved.
1. Graph1 #
Challenge Description #

Accessing the Website #
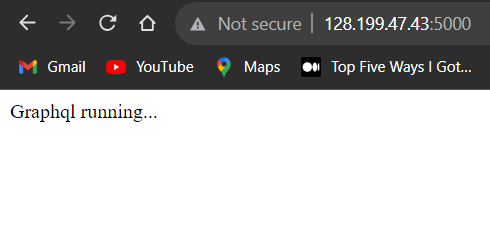
- We are brought to the above web page that tells us that Graphql is running.
- Graphql is a query language for APIs and a runtime for fulfilling those queries with your existing data.
Solution #
- We can use a Graphql query to fetch information about available types and fields like below
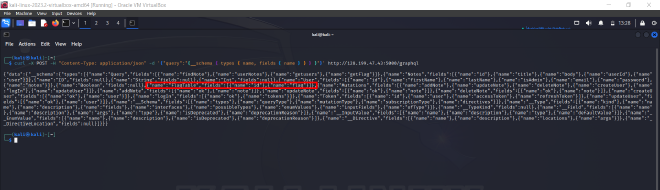
- We see a
TypenamedFlagTablefrom the result.
Exploring the FlagTable Type. #
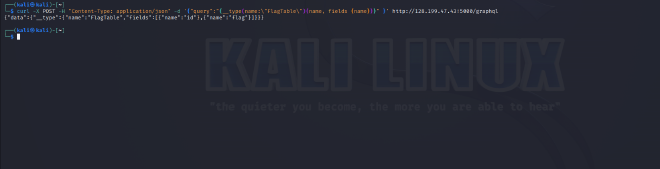
- We get
FlagTablewithidandflagfields. - We can query for the flag like this:
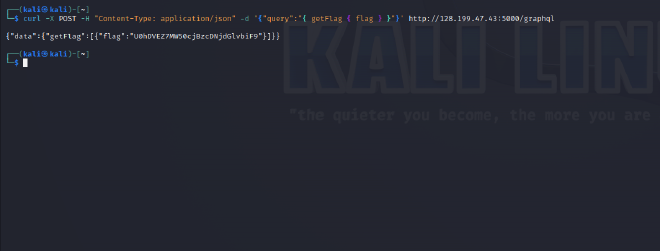
- The flag has been encoded using base64 and we can decode in Kali like this:
base64 -d U0hDVEZ7MW50cjBzcDNjdGlvbiF9We get our flag! SHCTF{1ntr0sp3ction!}
2. Snifferdog1 #
Challenge Description #
Analysis Using Wireshark #
- Opening the pcap file using Wireshark, we can apply the following filter .
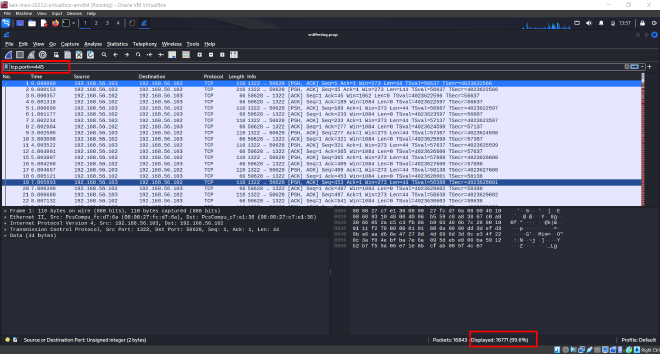
- Also, we can also see the total number of packets displayed, which is what we are looking for. That was easy!
3. Snifferdog2 #
Challenge Description #
Solution #
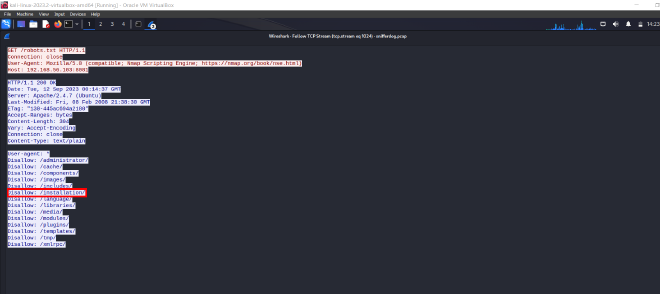
- We can apply the following filter:
(ip.addr == 192.168.56.103 || ip.dst == 192.168.56.103) && tcp.port == 8081 && http && http.request.uri contains "robots.txt"
Following the TCP stream, we get our flag!
That’s all for today :)