Patriot CTF 2023 (Part 1)
·4 mins

Table of Contents
Introduction #
- Patriot CTF was an online jeopardy style CTF hosted by George Mason’s University cybersecurity club, Mason CC.
- I participated in the CTF alongside my team, Fr334aks-Mini, and this is the write-up for the challenges that I was able to solve.
1. Patchwork #
Challenge Description #
- We have been given a
patchworkfile and the pogram should give the flag but there is an error in the code that prevents it from jumping to the correct function.
Initial Analysis #
- Let’s examine the file type using the
filecommand as shown below: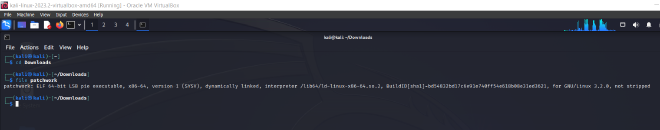
- We can see that the file is a 64-bit ELF(Executable Linkable Format) pie executable for x86-64 architecture. The file is dynamically linked, and is intended for use on a GNU/Linux system version 3.2.0 or later, with debugging information not stripped.
Static Analysis #
- To gain deeper insights into the binary’s functionality let’s do some static analysis with Ghidra
Analyzing Functions
- Given that the code’s ultimate purpose is to reveal the flag, we should be particularly interested in functions that might be doing this task.
- From Ghidra, let’s have a look at the program’s functions.
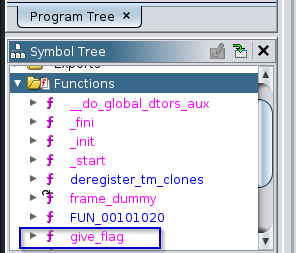
- We can see that there is a function named
give_flag. - With this function we can make an educated guess that our program should jump to that function and when the function is executed, that’s when we should get our flag.
- A close examination of the decompiled
mainfunction gives us another hint.
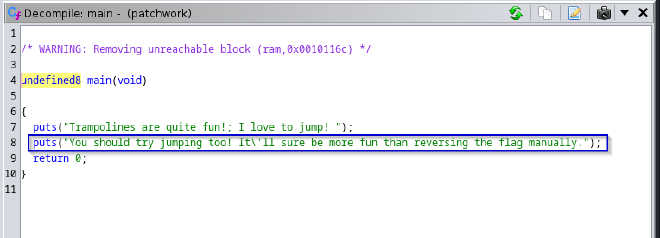
- It’s also worth noting that the
give_flagfunction has not been invoked anywhere in themainfunction
Dynamic Analysis #
- With the information and hints gathered so far, we can shift our approach to dynamic analysis and see whether we can make the program reach the
give_flagfunction. - We are going to use GNU Debugger (GDB).
1. Running GDB with patchwork
- First, we start GDB and load
patchworkprogram for debugging.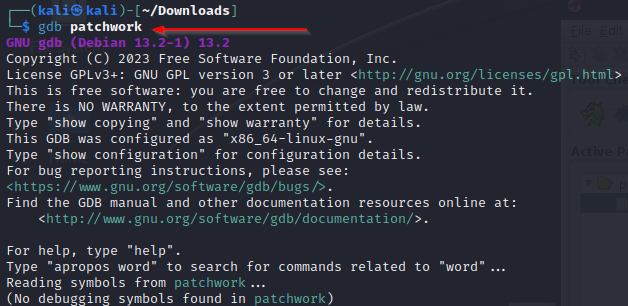
2. Setting a Breakpoint at main
- Next, we set a breakpoint at the
mainfunction using thebreakcommand. Setting a breakpoint at main is a common practice as it allows you to start debugging from the beginning of your program. It’s going to tell GDB to pause the program’s execution as soon as it enters the main function.
Setting a breakpoint at main is a common practice as it allows you to start debugging from the beginning of your program. It’s going to tell GDB to pause the program’s execution as soon as it enters the main function.
3. Running the Program
- With the breakpoint set, we initiate the execution of the program using the
runcommand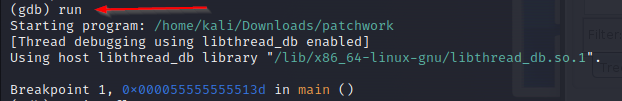
A Quick Summary of What is Happening
- GDB launched our “patchwork” program, and it stopped at the breakpoint we set in the main function. This pause allows us to inspect the program’s state and variables before they are modified by the program’s code.
4..Using the jump Command to Reach give_flag function
In this step, we use the jump command to change the program’s execution point to the function named give_flag:
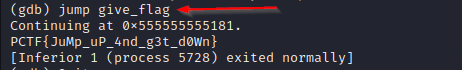
- This command instructed GDB to bypass all the code between the current program position (inside the
mainfunction) and thegive_flagfunction and … we get our flag! PCTF{JuMp_uP_4nd_g3t_d0Wn}.
2. Scavenger Hunt #
Challenge Description #
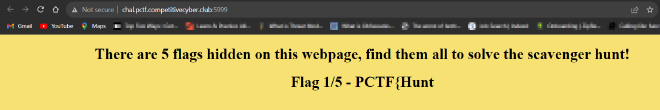
- We have been provided with
Flag 1/5and we need to find the remaining 4.
Viewing the Source Code #
- Let’s view the source code.
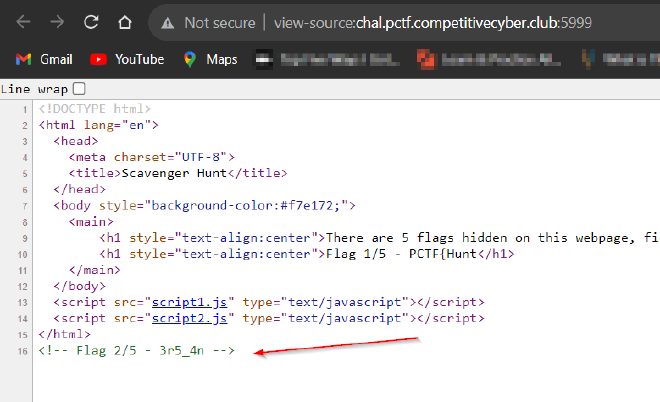
- We get flag 2!
- From the source code, we can see
script1.jsandscript2.js. It’s a good idea to check them.
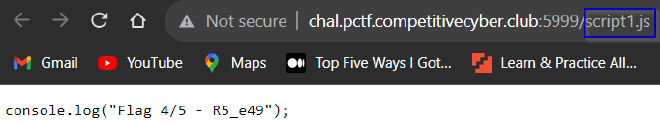
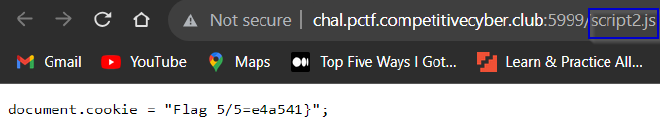
- We get Flag 4 and 5!
robots.txt file #
Let’s check the
robots.txtfile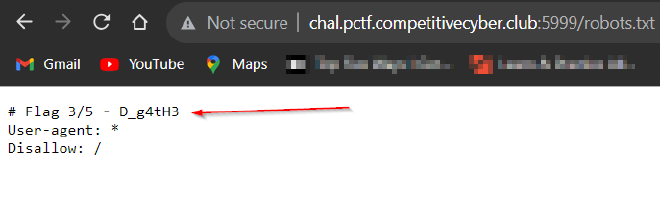
We get Flag 3!.
Reconstructing the flag we get PCTF{Hunt3r5_4nD_g4tH3R5_e49e4a541}
That was easy!
3. My Phone #
Challenge Description #
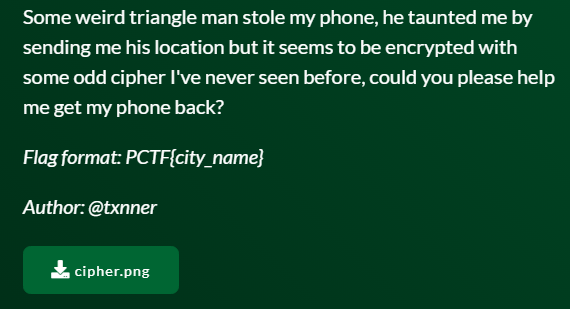
- We are given a file
cipher.pngshown below.
- This cipher is a substitution cipher that uses symbol substitution. The cipher is Gravity Falls Bills Cipher. We can confirm that here
Decryption #
- Using an online tool like dcode.org, we can decrypt the ciphertext.
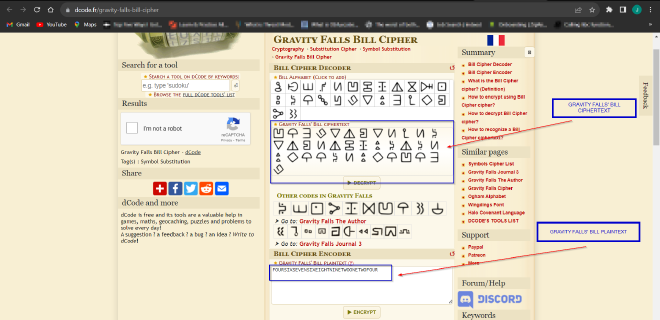
- We get
FOURSIXSEVENSIXEIGHTNINETWOONETWOFOURwhich is equivalent to4676892124. Adding the periods, comma and the -ve sign we get46.768,-92.124, and these are the coordinates that we are looking for! Using Google Maps, the city name isDuluth, which is our flag :).
See you in the next blog