CSAW CTF 2024
Table of Contents
Introduction #
- This was an online jeopardy-style CTF held from Fri, 06 Sept. 2024 — Sun, 08 Sept. 2024.
1. Baby Rev #
- You can get the file here
Enumeration #
- We download the binary and examine the
file typeusing thefilecommand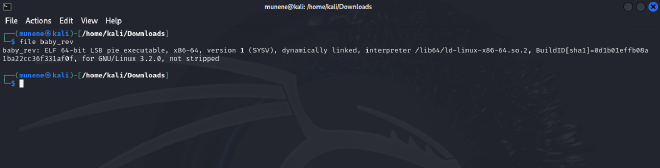
- The file is a
64-bit ELF pie executablefor x86-64 architecture. - The file is
dynamically linked, and is intended for use on a GNU/Linux system version 3.2.0 or later, withdebugging information not stripped. - We can check the
security features compiled into the binaryusingchecksec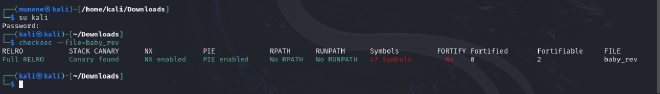
- We have
Full RElROenabled, astack canaryfound,NX bitenabled andPIEenabled meaning that the binary has the common buffer overflow protections. - Running
stringson the binary, we get the following which dont provide us with much:
Static Analysis #
Analysis Using Ghidra #
We decompile the
mainfunction in Ghidra, do somevariable renamingand we then can start making sense of what the program does: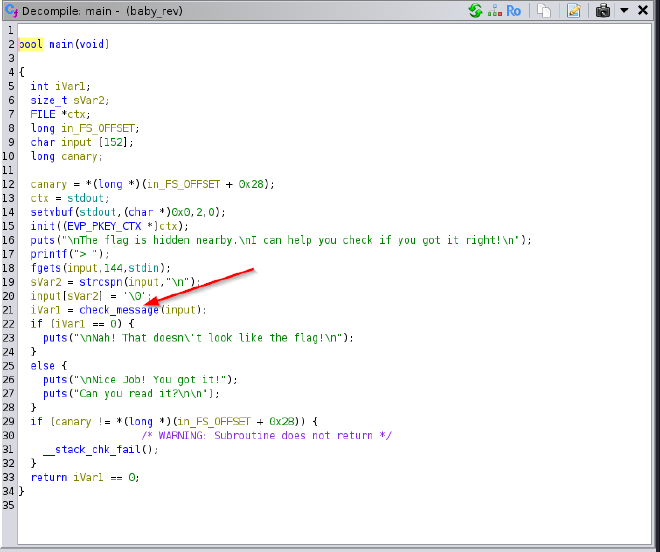
The program declares some variables then includes a
stack canaryto detect buffer overflows.The program then outputs a message on stdout, reads user input and removes the newline character then checks if the input matches the expected flag using a
check_messagefunction as seen online 21.If the
check_messagefunction returns 0 it prints a failure message else it prints a success message.The program terminates if stack corruption is detected.
Dropping into the
check_messagefunction: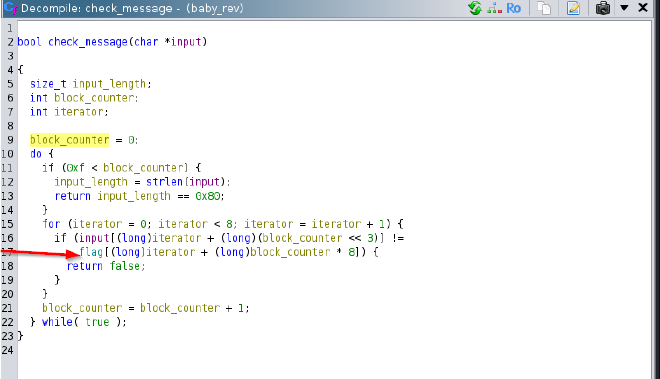
We can see an interesting variable named
flagonline 17Reversing the binary statically didn’t yield much, so I jumped into dynamic analysis to see how the program behaved when supplied with input.
Dynamic Analysis #
- Executing the binary like below made the program to exit with the failure message
python3 -c "print('A'*300)" | ./baby_rev
Debugging with GDB #
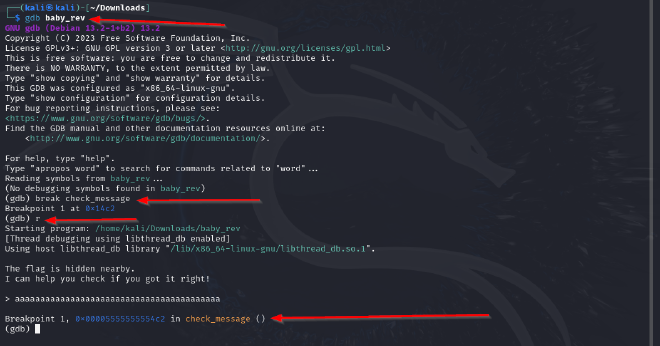
- We load the binary into
GDB. - Next, we set a breakpoint using
break check_message. - We run the program and provide an input when prompted.
- When we hit enter, we hit the breakpoint at
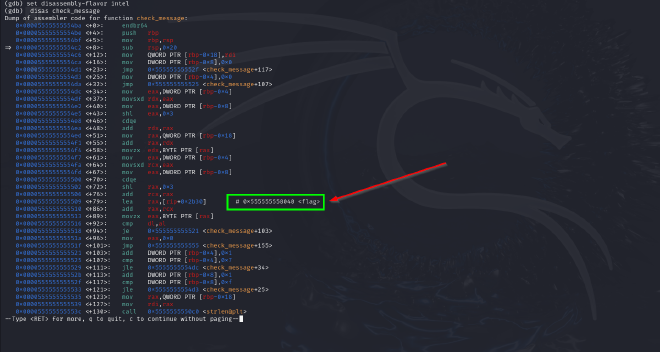
check_message. When we disassemblecheck_message, we can see this instructionlea rax,[rip+0x2b30] #0x555555558040 <flag>.
Summary #
- This instruction loads the memory address
rip + 0x2b30intorax. - The computed address is
0x555555558040, which is associated with the label<flag>.
Examining Memory #
x/s 0x555555558040in gdb will examine the memory address0x555555558040and display the string stored at that location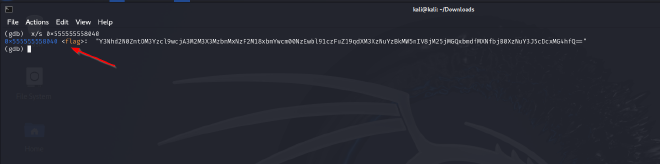
- And voila! We get our flag encoded into
base64
Base64 decoding #
- We copy it and save it as
flag.txtthen decode in Kali like below: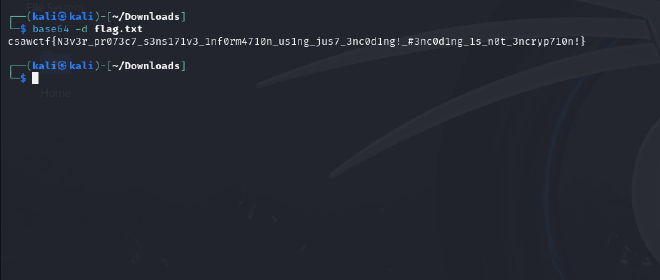
Conclusion #
{N3v3r_pr073c7_s3ns171v3_1nf0rm4710n_us1ng_jus7_3nc0d1ng!_#3nc0d1ng_1s_n0t_3ncryp710n!}
- Until next time :)